![[Nile TV] Finding The Right Coaches](https://abdomagdy.com/wp-content/uploads/2024/04/13-750x350.jpg)
[Nile TV] Finding The Right Coaches
In this engaging interview on Nile TV, Mr. Abdo Magdy, a technology executive, joins the host to explore the critical role of coaching in personal and professional development. The discussion delves into how coaches differ from therapists or mentors, why selecting the right coach is essential, and practical advice for choosing a coach, particularly for entrepreneurs and startup leaders. Watch the full interview on YouTube for more insights!
How do coaches help, and how are they different from therapists or friends?
Yeah, that’s a very good point. I think one of the big challenges once there is a coaching relationship established is understanding what to expect from the coach. So, in terms of what do you expect from the coach, I think the biggest word is going to be performance because coaches are focused on helping you become better at doing something specifically. If we’re talking about young entrepreneurs or business executives, it’s about executing the business and moving the business forward. So, it’s about focusing on the different areas of performance for a specific individual, being empathetic with them, and then helping them move to the next level. So, focusing on performance and performance improvement is a vital keyword here when it comes to what we expect from coaches.
Why is choosing the right coach a decisive factor in accomplishing goals?
Yeah, I think if we look at the process of improvement, coaches are a very, very important and intimate relationship to a lot of extents. If we look at those in sports, we would see that there is a huge difference that’s made in a player’s performance based on the kind of coaches that they have. So, if we look at this close relationship between coaches and crew chiefs, we would see that this is a very strong and important relationship, and based on that, looking at the right coach would be very vital to how far we’re going to go with that. So, for us to find the right coach, this is going to be affecting our performance. This could be like reaching the goal faster, so becoming better faster. I mean, even if we look at sports, I know people who were interested in a specific sport; they spent three years pursuing that path, and then that improvement was not really fast enough, but with the right coach, they were able to reach that kind of performance in like six months. So, saving time, saving money, and improving fast and rapidly, I think these are the benefits of finding the right coach.
What are the qualifications of a good coach, and how can we choose the right one?
Yeah, that’s a very difficult part to actually discover before having the experience itself. So, one of the best things to do is to actually know what you’re looking for and also look for specialized coaches. I think there are generic coaches; people can coach you across, like, there are life coaches, there are business coaches, and there are some deeply vertical and specialized coaches. And I think it’s going to also depend on who’s seeking the coaching and to what extent is the problem wide or is it narrow. So, based on that, you’re going to figure out what kind of coach you’re going to be aiming for. So, if I look at picking the right coach, I would actually understand what do I expect from the coach, what is the outcome that I’m seeking. So, if I’m an entrepreneur, for example, seeking to raise funds for my business, I would see that the outcome is for me to be qualified to talk to investors and secure funding for my business. So, this is my objective, and by then, I’m going to be looking for the coach who actually knows that topic, who has access somehow and understands the process and probably went through it before. So, if I find someone with that, I would possibly just look for a meeting, an introduction meeting with them. And I think lots of professional coaches offer that—you can spend one to two hours with them having an introduction meeting without committing to a coaching relationship. So, having this kind of dating relationship, in which you sit with the coach and you see whether you’ve got chemistry, do you like to talk with this person, would you trust them with your secrets? This is a very vital step. One other aspect is looking at others from the industry and what kind of feedback they have from this particular individual.
What is the difference between a mentor and a coach?
Yeah, I think the mentor is more like a spiritual relationship to what extent that mentor is someone that you look up to and who accomplished something, and then you have mostly less frequent organization than a coach. The mentor is someone who provides general direction, like advice when it comes to general direction. So, which direction should I take? So, a mentor would be someone who could possibly be more senior, like older, with a lot of experience, someone that you look up to as a character and as an individual, and by then, they provide you in conversation about the general direction. So, there’s a lot of things in common with coaches, but coaches are mostly focused on performance and specific goals. So, if you hire a coach because you have a very particular objective that you want to reach, then this coach, while not guaranteeing that you’re going to reach that goal because that’s something outside of their control, they do their best in getting you as fit as possible to reach that goal. So, this is a distinction between the mentorship and the coaching relationship.
How can coaching benefit startups, and what is the nature of the relationship between entrepreneurs and coaches?
Getting back to your question, when it comes to focusing on startups, I think by then a coach would better actually be focused on a specific individual within the company. So, there could be group coaching for a whole startup, but it’s going to have a different format. I think some of the best ways to do that is to either coach the CEO or coach the management team, even sometimes independently, because people sometimes have different agendas, and a coach has to be committed to a specific individual. So, the highest value could be from coaching the CEO himself, and also, I could have a coach, everyone else within a team could get a different coach, but by then, if you focus on the performance of the CEO, the way they look at the business, the way they interact with people, and also possibly bringing a network of people to kind of grab and motivate the CEO in a specific direction, I think that would be an extremely valuable thing, just spotting on a specific individual, because this is somehow an intimate relationship. And yes, when it comes to startups, because startups are evolving organizations, there’s massive risk and massive change and a lot of uncertainty, so it gets very intimate sometimes. And I think some of the downside is that there are massive expectations of what the coach is going to bring us. So, if we’re building a startup with an idea and we’re seeking funding, I might assume that my coach is going to possibly just give me access to the funds, while the coach can actually help you become more ready to access the funds; you cannot guarantee that. And also, there are many variables; it has to do with verifying that this is actually a feasible business idea, and this might not be the area in which you have requested the coach to coach—you might be performance-oriented, and they are not necessarily looking at the strategy of the company. So, understanding, while this is going to become personal and intimate, is that this is what I provide you, and sometimes, as coaches, you have to repeat that. In this part, you probably need to talk to a therapist—I can connect you to a therapist—or I can connect you to a consultant, but when it comes to that, I’m concerned about you and your performance with the business, and that’s what we’re going to focus on during the sessions. So, you would think about it pretty close to therapists when it comes to good coaching; they’re going to become more intimate, but it’s actually focused on performance—what do I do in order to get there.
How can I know the coaching program and format that fits my needs?
Yeah, I think some of the best things is to have this customized. So, coaches offer specific programs; this could actually be time-based, mostly it’s time-based because in a coaching interaction, what you do is quite different and a lot different context. So, you need to actually look at it in terms of what time do I have as an executive because if I’m a CEO of a startup, I’m probably very busy. If I have 10 or 20 staff and I’m recruiting heavily, so I’m possibly busy, and my coach is also busy. So, I need to look at what kind of time limits do I look for.

![[Nile TV] Cybersecurity Threats, What you need to know](https://abdomagdy.com/wp-content/uploads/2024/04/16-750x350.jpg)


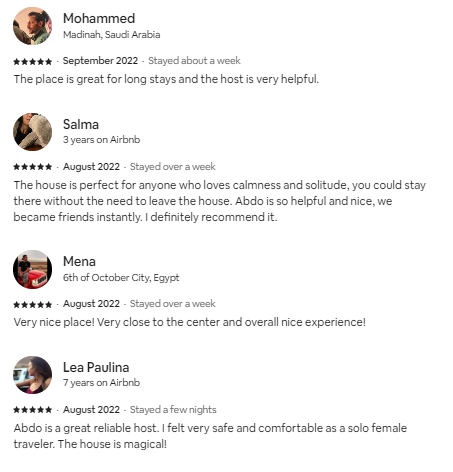
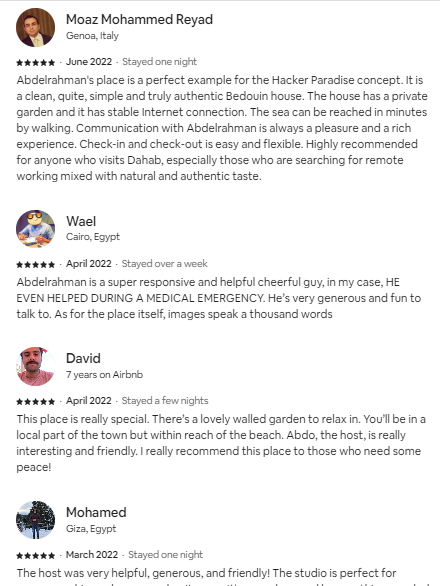
![[2022] Al-Basateen, Building Sustainable Living Communities in Egypt’s Sinai, Karm Hospitality](https://abdomagdy.com/wp-content/uploads/2024/09/Al-Basateen001-495x350.jpg)


![[2020] [Project] [Egypreneur] #COVID19 Business Continuity Emergency Response](https://abdomagdy.com/wp-content/uploads/2024/09/covid19-campaign-750x350.png)





























![[2019] [Project] [Egypreneur] Automated Funding Assistant, Business Builders’ One-Stop-Shop.](https://abdomagdy.com/wp-content/uploads/2015/10/VT-cropped-491x350.jpg)
![[2019] [Project] [JV] Digital Transformation for the Oldest Standing Tourism Company in Egypt](https://abdomagdy.com/wp-content/uploads/2019/12/EastMarPartnership-750x350.png)



